Introduction
 |
 |
 |
|---|---|---|
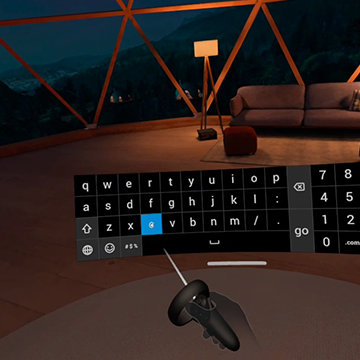
| Figure 1: An increasing number of devices can benefit from knowing the user’s identity to allow for adaptation and personalization (left). While passwords still dominate for over 60 years now, they fall short in terms of usability and user experience, as they increasingly overwhelm users mentally, and entering them on many devices is cumbersome, for example, in virtual reality (middle). Behavioral Biometrics is becoming a viable alternative to traditional authentication schemes and supersedes their counterparts (e.g., traditional biometrics such as fingerprint scanners (right)) in terms of user experience and usability as they often do not need explicit interactions but are implicit instead, allowing for continuous authentication. | ||
With today’s computing devices’ ubiquity and their overall increasing number, the number of times a person has to prove their identity per day to a computing system is also ever-increasing. Proving one’s identity to a computing system (i.e., the process of authentication) is critical to ensure security and data privacy on the device. Additionally, knowing the user’s identity also allows for personalization and adaptation of the device; hence this information is almost always required in any computing system used by humans. Consequently, the trend of “ubiquitous computing” demands “ubiquitous authentication” in everyday life as well.
Users who interact with a computing device do so by usually following a primary task. However, the execution of the primary task is often interrupted by a required explicit interaction demanded by the device from the user. For example, the task of sending a message on a smartphone to another person is interrupted by the lock screen that demands the entry of a Personal Identification Number (PIN) from the user after the smartphone is activated and before the message can be sent. Nevertheless, with each device, the process of authentication is subject to the device’s sensing capabilities, which vary widely; for example, proving one’s identity to a website displayed on a notebook is widely different compared to authenticating on a smartwatch, which offers different input modalities. Traditional biometrics (e.g., fingerprints) are often similar to PINs or passwords in terms of demanding user’s explicit interactions, such as having them move their finger explicitly to a fingerprint scanner.
Behavioral Biometrics in contrast promises to ease this process as they often can be elicited in an implicit way from the user without the user having to actively deal with the authentication system (e.g., user’s typing behavior on smartphones s [3, 4], their interactions in virtual reality [5, 7–10], or gaze behavior [6]).
For over sixty years, passwords have been the primary method used for authentication. Yet, there exists a wide consensus that passwords are insecure, and users are increasingly overwhelmed by them [2]. As a consequence, alternative methods for user authentication moved into the focus of research, where particularly Behavioral Biometrics has become a viable alternative, as they are very well suited for implicit and continuous authentication, which bear unique quality attributes and promise an enhanced user experience and usability [2].
Unique Benefits of Behavioral Biometrics
Utilizing Behavioral Biometrics is particularly beneficial for two reasons. First, they allow for implicit authentication, which means that they are particularly well suited to detect their user’s identity without demanding explicit actions from the user [2]. Instead, implicit authentication methods use behavioral characteristics of the interaction that users perform with regard to their primary task for authentication [2]. Thereby, they can ideally authenticate users without interruption seamlessly in the background [2]. This is practical for usability, as users do not have to invest time in interacting with the authentication process. It also benefits their user experience, as their primary task is not interrupted.
Second, as the device can implicitly sample the user’s behavior, the device can authenticate the user continuously [14]. Continuous Authentication (CA) stands in contrast to static authentication, which is currently most often performed [14]. In static authentication, the device checks the user’s identity at the beginning of a session and unlocks itself [14]. However, if another person starts using the device, it will remain unlocked for that person. Continuous authentication changes this security issue, as a continuous authentication system frequently checks the current user’s identity implicitly based on their behavior. Thereby, the device can lock itself by recognizing that another person uses it, effectively increasing security over what static authentication can offer.
Scope of Course
We first provide the theoretical foundations of authentication, connected aspects, and terms concerning their utilization in intelligent user interfaces. We do so by pointing out their strengths and weaknesses to aspects connected to Human-Computer Interaction (HCI), such as their implications for usability, user experience, and the system’s security. We furthermore point out key aspects to consider when creating novel academic works within the domain, which we underline with key elements elicited from the scientific community and provide guidance around typical pitfalls. Finally, we complete the course with an introduction to machine learning approaches for Behavioral Biometrics, covering the steps of data analysis, visualization, preprocessing, models, and metrics.
